Comprehensive Cyber Security Consulting Services Essex: Protect Your Information
Comprehensive Cyber Security Consulting Services Essex: Protect Your Information
Blog Article
Empower Your Company WITh Dependable IT Assistance Solutions and Cyber SecurITy Solutions
In today's rapidly advancing electronic landscape, the foundation of an effective company exists in the seamless integration of trustworthy IT support solutions and durable cybersecurity solutions. With the rapid development of online risks and the boosting intricacy of technological systems, companies deal with a pressing demand to strengthen their facilities against prospective susceptabilities. By leaving your IT needs to proficient specialists and executing aggressive cybersecurity actions, you can secure your procedures, shield sensitive information, and maintain an one-upmanship out there. The trick to unlocking the full capacity of your organization hinges on the tactical positioning of technology with your business goals, making sure a durable and safe and secure structure for continual development.
Significance of Trustworthy IT Assistance
In today's digitally-driven organization landscape, the value of trusted IT sustain can not be overstated. Businesses rely greatly on innovation to operate efficiently and effectively. From maintaining networks to fixing technological problems, having reputable IT support guarantees that procedures run efficiently without considerable disruptions.
Among the main reasons that reputable IT support is vital is its role in reducing downtime. Any technological glitch or system failing can stop business procedures, resulting in lost efficiency and revenue. With reliable and timely IT support, these problems can be dealt with swiftly, lessening downtime and its connected prices.
Moreover, dependable IT sustain plays an essential function in enhancing cybersecurity. In a period where cyber risks are rampant, having a team of IT specialists guarantees that systems are sufficiently protected from prospective violations. These experts apply robust protection actions, screen systems for any suspicious tasks, and offer prompt updates to safeguard versus advancing cyber dangers.

Benefits of Cybersecurity Solutions
Offered the vital duty of trusted IT support in minimizing downtime and improving cybersecurity, it is essential to highlight the significant advantages that cybersecurity solutions bring to businesses in today's electronic landscape. Cybersecurity options play an essential function in safeguarding delicate information and protecting services from cyber hazards.
Additionally, cybersecurity remedies help services follow sector guidelines and criteria, reducing the threat of non-compliance charges. They likewise improve overall operational performance by providing a secure setting for carrying out on-line deals and interactions. In addition, cybersecurity remedies make it possible for services to find and respond to cyber incidents without delay, lessening the effect of prospective protection breaches. Inevitably, purchasing cybersecurity services not only protects companies from cyber dangers yet additionally contributes to their lasting sustainability and growth in a significantly electronic world.
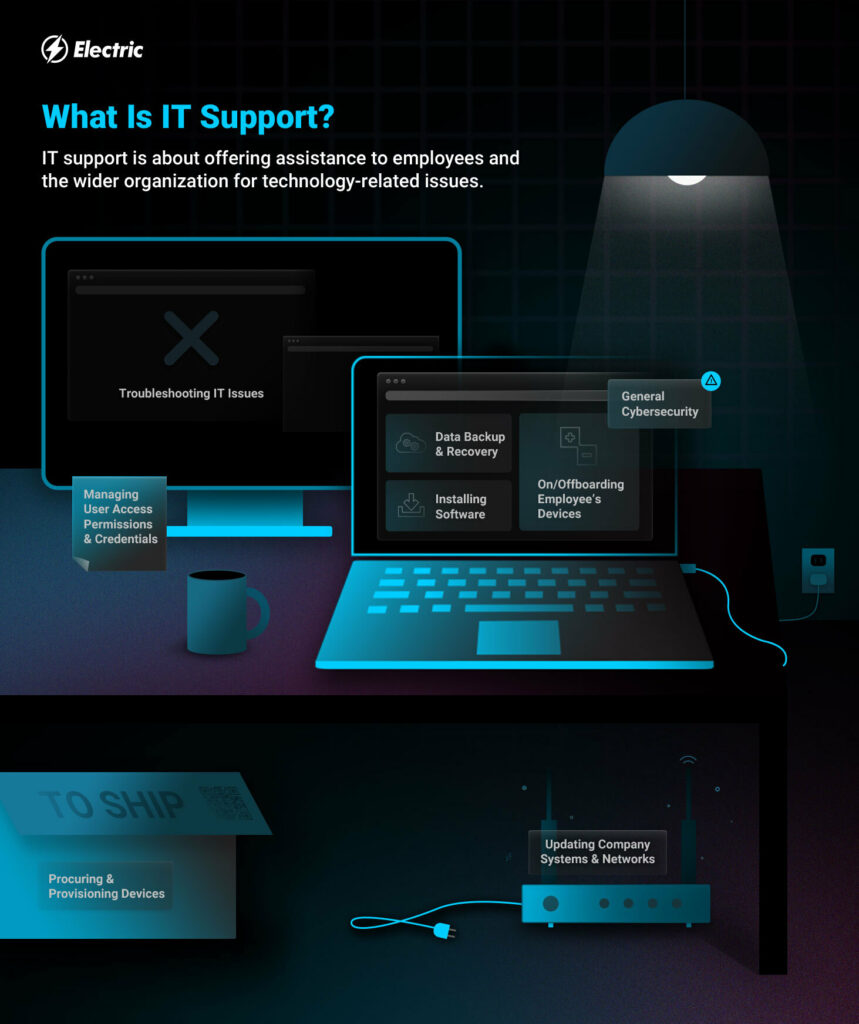
Selecting the Right IT Provider
To successfully meet the technological needs of your service, selecting the ideal IT services is vital. When picking IT services, it is crucial to take into consideration numerous vital factors to make sure that the solutions line up with your business goals. Begin by assessing your particular demands and purposes to establish the sort of IT services that will best support your procedures. Consider the scalability of the IT services to accommodate your service's development and advancing requirements. Seek a service company with a proven performance history of reliability and competence in the services you require. It is also essential to review the level of client support offered by the IT company to ensure that you will get prompt help whenever required. In addition, consider the cybersecurity steps find more information and protocols executed by the company to protect your company data and systems. By very carefully evaluating these facets, you can pick the appropriate IT services that will encourage your business and drive success.
Carrying Out Cybersecurity Steps
Applying durable cybersecurity procedures is a vital element of safeguarding your company's sensitive information and making sure the stability of your systems. Cyber dangers proceed to progress in class and regularity, making it essential for businesses to proactively secure themselves.
Employee training is likewise critical in reducing cybersecurity dangers. Enlighten your personnel on best practices for data taking care of, acknowledging phishing efforts, and keeping solid password health. Developing clear plans and treatments for event action and data breach administration is necessary to decrease the effect of any safety and security violations. Normal security audits and penetration testing can further evaluate the effectiveness of your cybersecurity procedures and identify locations for improvement. By prioritizing cybersecurity and staying positive in your approach, you can much better secure your service from cyber dangers and potential information violations.
Ensuring Organization Connection
After implementing durable cybersecurity steps to guard your business's sensitive read what he said information, the focus changes in the direction of making certain organization connection despite potential disturbances. Service continuity preparation is vital for alleviating threats and preserving operations throughout unanticipated occasions such as natural calamities, cyber-attacks, or system failures. One vital facet of making certain service connection is the growth of an extensive connection plan that lays out techniques for keeping crucial features and services. This strategy ought to incorporate treatments for information back-up and recovery, different interaction approaches, and employee functions and responsibilities throughout a situation.
Organizations need to carry out drills and simulations to recognize weak points in the plan and make required improvements. By focusing on company connection, companies can enhance their strength and lessen the influence of possible threats on their operations and track record.
Final Thought

In today's rapidly progressing electronic landscape, the foundation of an effective service lies in the seamless combination of reliable IT support services and robust cybersecurity solutions.Provided the vital role of dependable IT sustain in minimizing downtime and enhancing cybersecurity, it is important to highlight the considerable advantages that cybersecurity solutions bring to companies in today's electronic landscape.After implementing durable cybersecurity measures to protect your service's delicate data, the emphasis changes in the direction of guaranteeing service continuity in the face of possible interruptions.In final thought, trusted IT sustain services and cybersecurity services are essential for equipping services to operate effectively and safely. It is crucial for organizations more tips here to prioritize investing in IT sustain and cybersecurity to secure their procedures and keep a competitive edge in today's digital landscape.
Report this page